Signal Owl Basics
The Signal Owl is a simple payload-based signals intelligence platform with a unique design for discreet planting or mobile operations on any engagement.
This getting started guide video only applies to Signal Owl firmware version 1.0.0. From version 1.0.1 onwards, entering arming mode is accomplished by pressing the button any time during attack mode (roughly 1 minute after power-on). Continue reading.
SOFTWARE BASICS
Many popular tools, such as Kismet, Nmap, MDK4 and the Aircrack-ng suite as well as bash and Python 3 are included. Using these and the Owl framework, the pentester may execute bash payloads with Ducky Script loaded from an ordinary USB flash disk.
DEPLOYMENT
The Signal Owl features a unique form-factor and is designed to function as a long-term wireless implant, or mobile operations in conjunction with a standard USB battery.
IMPLANT OPERATIONS
During long term wireless engagements, the Signal Owl may be planted inline between any typical 5V USB power source. This may be useful in situations where ports are occupied, or to deter the unit from being unplugged.
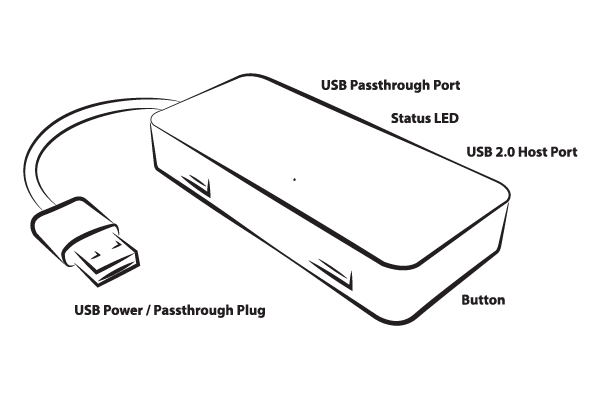
The Signal Owl is powered from the USB-A Male pigtail, while data and power are passed through to its USB 2.0 port closest to the pigtail. For example, with a keyboard or mouse plugged inline between this USB pass-through port and the pigtail connected to the target computer, the Signal Owl will not enumerate as a device on the operating system - only the keyboard or mouse will.
MOBILE OPERATIONS
The Signal Owl features a low power consumption profile, with a typical power draw averaging 100-200 mAh. Additionally, it is thermally optimized for long term deployments in many indoor environments. One can expect a large 20,000 mAh USB battery bank to operate the unit for up to 4 days.
MODES OF OPERATION
The Signal Owl has two basic modes of operation: Arming Mode and Attack Mode. By default the Signal Owl will boot into Attack Mode. To access Arming Mode, momentarily press the button on the bottom of the unit using a paperclip or similar instrument any time in the Attack mode (approximately 1 minute from power-on and after).
Version 1.0.0 Note: In Signal Owl firmware version 1.0.0, entering Arming Mode was achieved by momentarily press the button during a 3 second mode selection phase at bootup which was indicated by the rapidly blinking LED.
ARMING MODE
In Arming Mode, the Signal Owl will present the user with an open access point named Owl_xxxx (where xxxx is the last two octets of the devices MAC address) and will be accessible via SSH.
The open access point may be configured with WPA security by editing the /etc/config/wireless file and adding the following options to the config ‘wifi-iface’ section:
option 'encryption' 'psk2'
option 'key' 'secret passphrase'
ATTACK MODE
In Attack Mode, the Signal Owl will execute the following operations:
- If a payload is present on the root of a connected USB flash disk, it will be copied to the Signal Owl’s internal storage at /root/payload
- Similarly if an extension folder is present on the root of a USB flash disk, the contents of this folder will be copied to the Signal Owl’s internal storage at /root/payload/extensions
- The extensions will be sourced, and the payload on the Signal Owl’s internal storage will execute
- If no payload is found (on internal or external storage) the LED will indicate the FAIL status