PineAP
PineAP Capabilities
PineAP enables some of the core functionality of the WiFi Pineapple:
- Control access with Filters
Limit your engagement by configuring access by filters. Limit to specific clients or SSIDs, or exclude specific clients or SSIDs. - Impersonate APs
Explicitly advertise lists of access points to instigate clients into connecting to previously saved networks. - Open AP
Serve a basic, unencrypted Open access point, or automatically impersonate any Open access point requested by a client. - Evil WPA
Serve a new WPA network, or copy an existing WPA network. Capture partial handshakes to crack the WPA keys of unknown networks. - Evil Enterprise
Serve a WPA-Enterprise network with optional key exchange degradation. Coupled with automatic authorization of all accounts, identify misconfigured enterprise clients and capture credentials.
PineAP Settings
PineAP offers three basic operation modes:
- Passive
Collect information about nearby access points, and add them to the list of potential APs to advertise.
Accept connections to the Open, WPA, and Enterprise SSIDs (if enabled)
Do not advertise other access points, and it will not answer for other SSIDs. - Active
Collect information about nearby access points.
Actively advertise all SSIDs from the Impersonated AP Pool (if enabled)
Respond to all client requests for any network which is permitted by the filters. - Advanced
All PineAP features can be individually configured; mix and match the features you need.
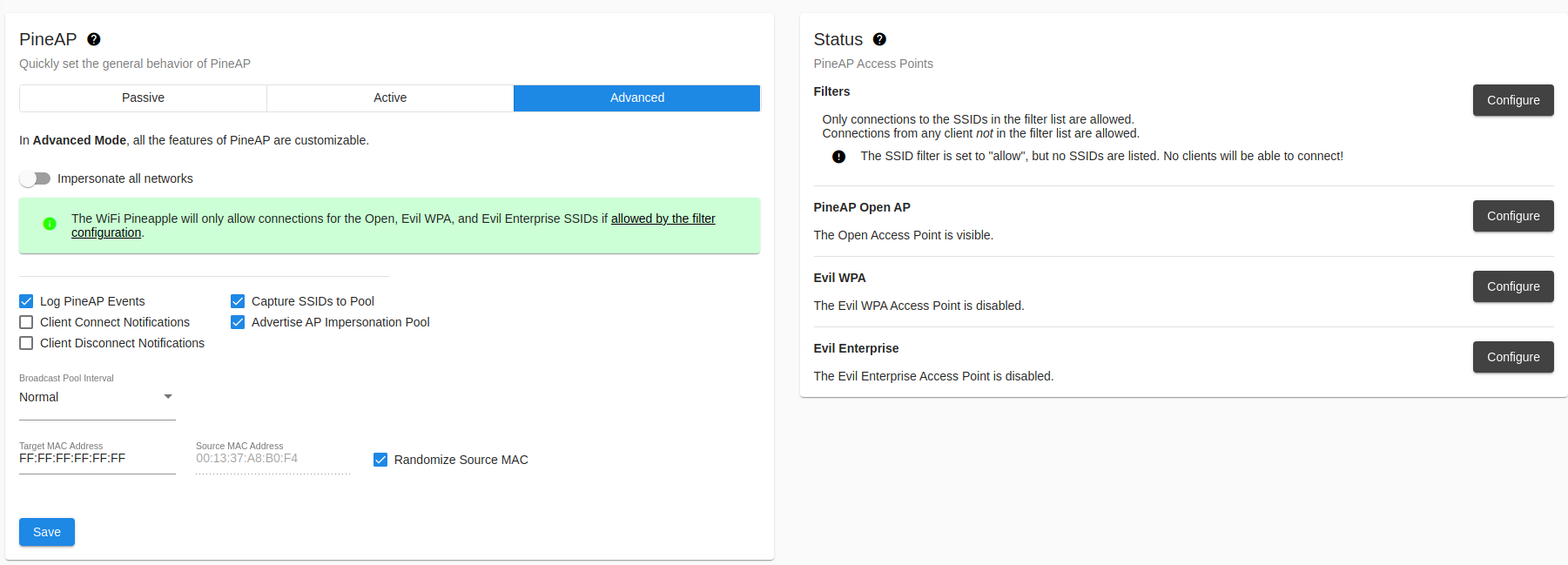
PineAP Settings
PineAP Event Logging
PineAP will log probe requests, associations, and disassociations to the system event log.
The event log can be viewed in the “Event Log” category in the sidebar menu.
Notifications
Create a notification in the WiFi Pineapple UI when a client connects or disconnects from any of the WiFi Pineapple access points.
SSID Pool Capture
Automatically add SSIDs to the SSID Pool for advertising. SSIDs are collected from probe requests made by clients and nearby access points observed by recon mode.
When “Capture SSIDs to Pool” is enabled, SSIDs seen passively (observed probe requests) and through recon mode are automatically added to the pool of target SSIDs.
Additional configuration can be found under the “Impersonation” tab.
Broadcast SSID Pool
SSIDs from the SSID Pool can be advertised; this will cause the SSIDs to be visible in the network list of nearby devices, and may be useful for collecting client information.
Additional configuration can be found under the “Impersonation” tab.
SSIDs can be impersonated from a single BSSID, or from a pseudo-random BSSID for each SSID.
Open SSID
The WiFi Pineapple can advertise a single Open SSID, or respond for any requested SSID that matches the filter rules.
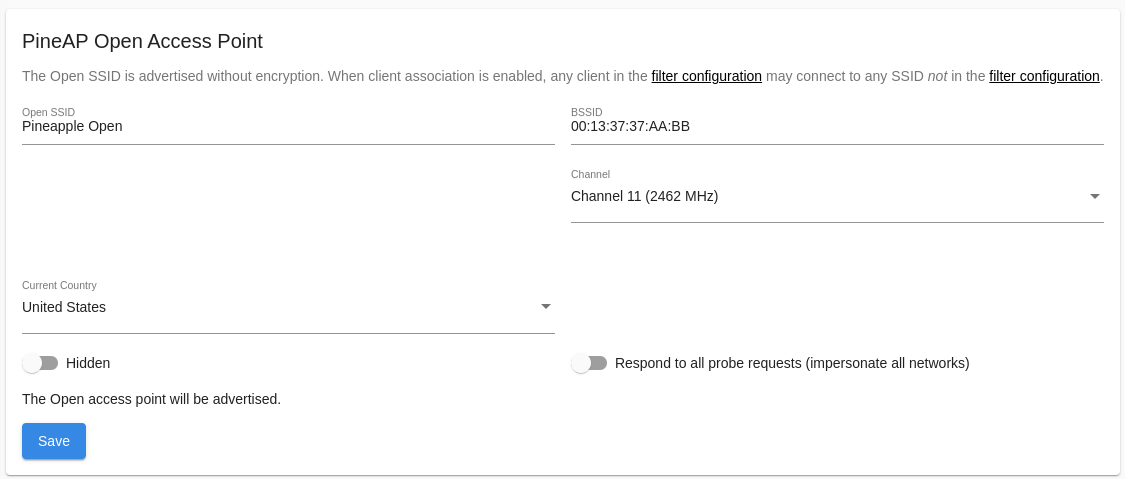
WiFi Pineapple Open AP Configuration
Basic Open Access Point
The basic Open access point can be configured as visible or hidden; a hidden access point does not advertise its SSID, but clients which have saved the SSID will still be able to identify it, and some tools may still reveal the SSID.
If you change your Open SSID from visible to hidden, any device with the network saved will still detect it as if it were visible, and will still probe for the name!
Hidden network SSIDs can still be discovered when a client connects, so don’t be surprised if you see your network show up in the SSID pool if collection is enabled!
Be sure to allow your Open SSID in the filter rules; it must be in the list if filters are set to “Allowed”, and must not be in the list if filters are set to “Deny”.
Multiple Open Access Points
When “Impersonate All Networks” is enabled, the WiFi Pineapple will answer for all SSIDs which are permitted by the filter configuration!
Filters can be used to tune the responses for your engagement, by either allowing all SSIDs in the filter list, or denying all SSIDs not in the filter list.
Evil WPA
The Evil WPA access point is used to impersonate a WPA (or WPA2) PSK network. It can also be used to collect partial handshakes for use with external cracking tools when the PSK is not known.
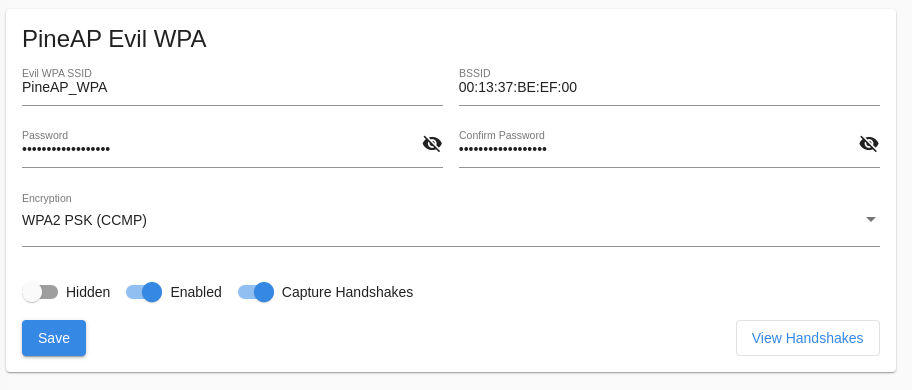
Evil WPA Configuration
Be sure to allow your Evil WPA SSID in your filter configuration, or clients will not be able to connect!
Collected handshakes will be added to the Handshakes area, where they can be downloaded in standard pcap or hashcat format.
Evil Enterprise
The Enterprise tab allows you to configure a WPA-EAP Enterprise rogue access point. To begin, fill in the form to generate the EAP configuration and certificates.
Enterprise, or EAP, WiFi authentication is typically used on corporate networks with per-user logins on the network. It is protected by a SSL certificate, which must be created first.
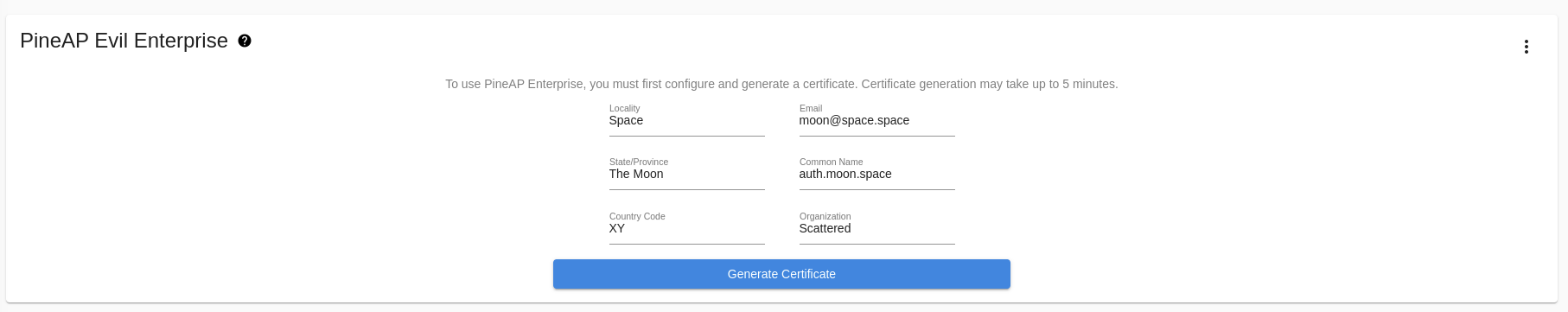
Enterprise certificate generation
Once the certificate has been generated, you’ll see easy to use options to configure the rogue enterprise access point, and view the challenge data any connected clients provide. Generating the certificate will take a moderate amount of time (sometimes up to 5 minutes) while the WiFi Pineapple gathers random data.
The information in the enterprise certificate is arbitrary. Some WiFi clients show the user the data entered in the certificate, while others may only show a certificate hash.
Properly configured WiFi Enterprise clients will reject unknown certificates, however many devices do not offer proper configuration and may either blindly accept new certificates, or prompt the user to accept the certificate.
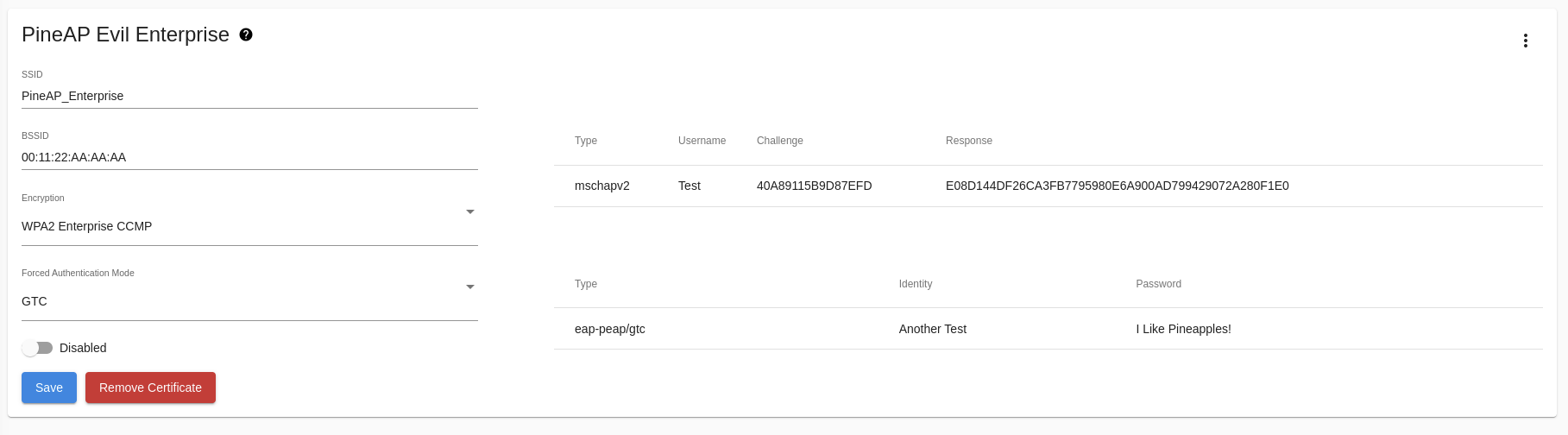
Evil Enterprise AP and Handshakes
Once configured, the Evil Enterprise will capture the challenge data or full passwords of clients which connect, depending on the authentication method used.
Be sure to allow your Evil Enterprise SSID in your filter configuration, or clients will not be able to connect!
Enterprise Authentication Methods
When advertising an enterprise network, the WiFi Pineapple supports three authentication types:
- Any
The WiFi Pineapple will allow a client with any authentication method to connect. If possible, the WiFi Pineapple will inform the client it is allowed to connect. Clients connecting with EAP-GTC will connect as normal and the user login saved, while clients connecting with EAP-MSCHAPv2 will receive an error, but the MSCHAPv2 hash challenge will be captured and logged. - MSCHAPv2
MSCHAPv2 is the most common authentication method for enterprise clients. A MSCHAPv2 client uses a hashed authentication method which does not disclose the password.
The WiFi Pineapple cannot answer the hash challenge without knowing the users password: A MSCHAPv2 client will not be able to fully connect to the WiFi Pineapple access point, but the challenge hash will be captured and logged, and can be processed offline to derive the user password. - GTC
GTC is a simpler authentication protocol. Clients using GTC will disclose the full username and password, and will connect to the WiFi Pineapple as normal. The username and password will be logged.
For maximum compatibility, leave the authentication method as Any; this will allow most client configurations to connect, but many will default to MSCHAPv2, which will not be able to fully connect to the Evil Enterprise AP.
To try to force clients to use a more vulnerable authentication method, switch to GTC. To capture hashes from clients which are configured to only support MSCHAPv2, use MSCHAPv2 mode.\
Impersonation
Some WiFi clients will not attempt to connect to a network unless they observe an advertisement; in addition to responding as any network when “Impersonate All Networks” is enabled, the WiFi Pineapple can advertise additional SSIDs using the SSID Impersonation Pool.
These networks will be visible in the network lists of nearby devices. Combined with “Impersonate All Networks”, this can capture clients which otherwise would not connect to the WiFi Pineapple.
Networks advertised from the SSID Impersonation Pool can come from any BSSID (that of the WiFi Pineapple Open access point, or any other MAC address), or from a pseudo-random BSSID which is unique to each impersonated SSID, and can be sent to the broadcast address (default), or a single client address.
To allow connections to a SSID from the impersonation pool, be sure it is allowed by your filter configuration and “Impersonate All Networks” is enabled!
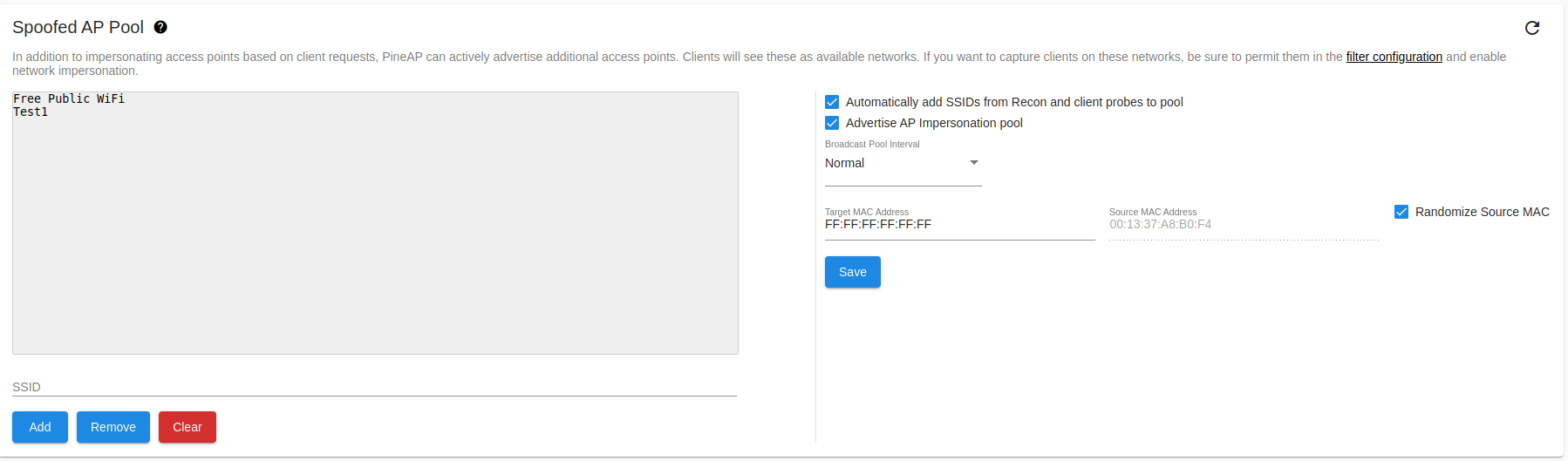
SSID Impersonation Pool
SSIDs may be manually added to the list, or automatically collected by the WiFi Pineapple from client probe requests and recon scan results.
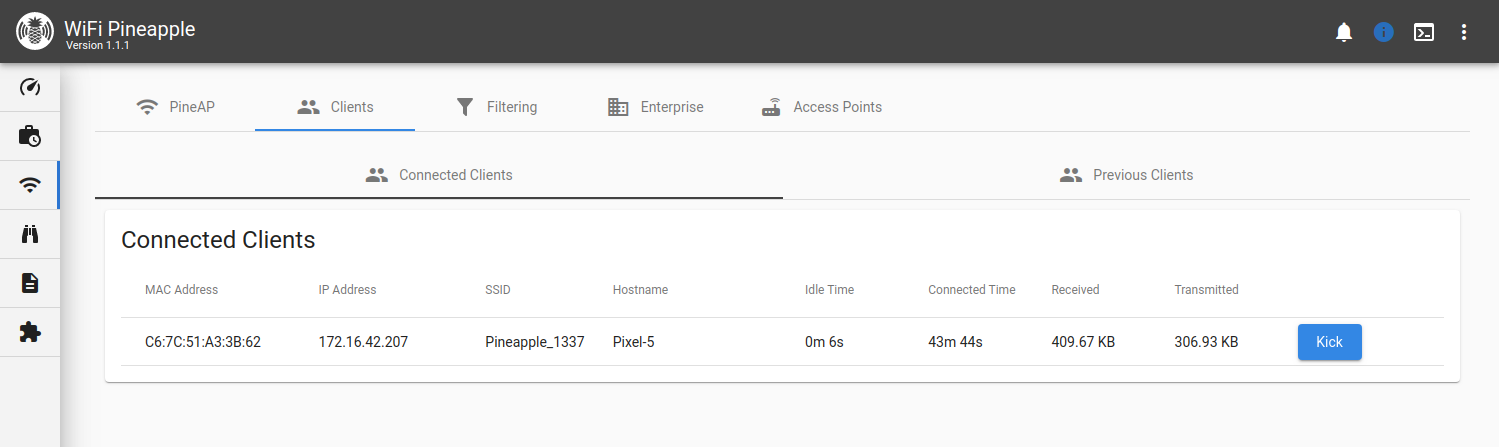
Clients
The clients page provides two views for clients, split into connected clients and previous clients. From the Connected Clients you can view information about each connected client, including MAC, IP Address and the SSID they associated to, as well as the ability to kick them from the network.
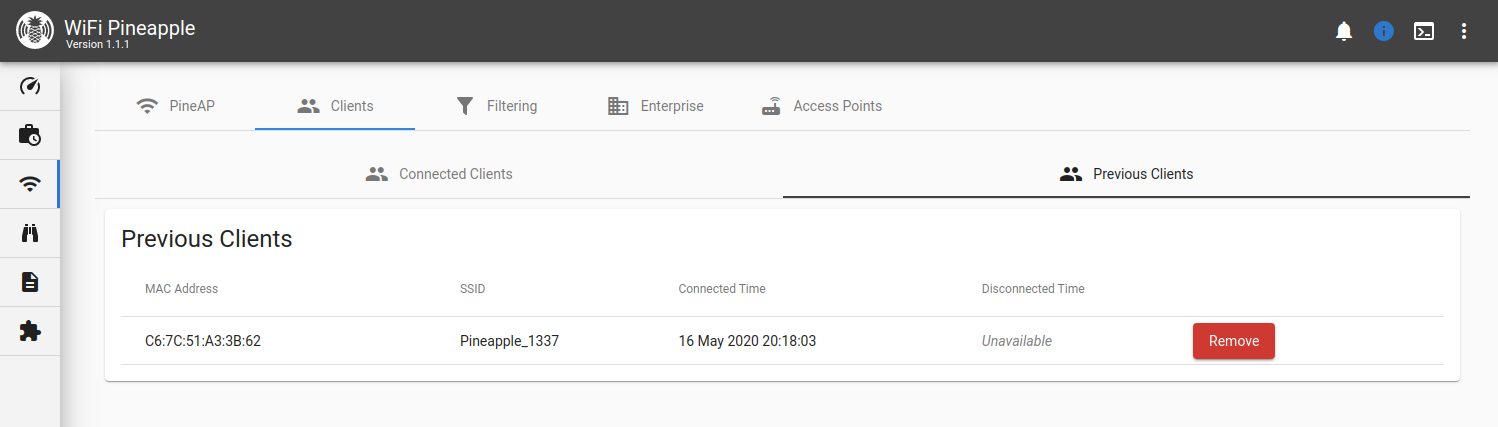
Switching to the Previous Clients tab shows you a record of all previous associations to the rogue access points hosted by the WiFi Pineapple. Clients that have not yet disconnected from the network have a disconnect time of “Unavailable”.
Filtering
The filtering page allows you to have fine control over what devices can connect to your WiFi Pineapple. You can do this by combining two filters: the Client Filter and the SSID Filter, with two modes each: Allow or Deny.
With the client filter you may limit the scope of engagement by choosing what devices may connect. Allow only specific devices, or any device that isn’t specifically on the deny list.
With the SSID filter you may specify the spoofed networks for which the WiFi Pineapple will allow associations. Allow associations for only specifically listed SSIDs, or any SSID that isn’t specifically listed.
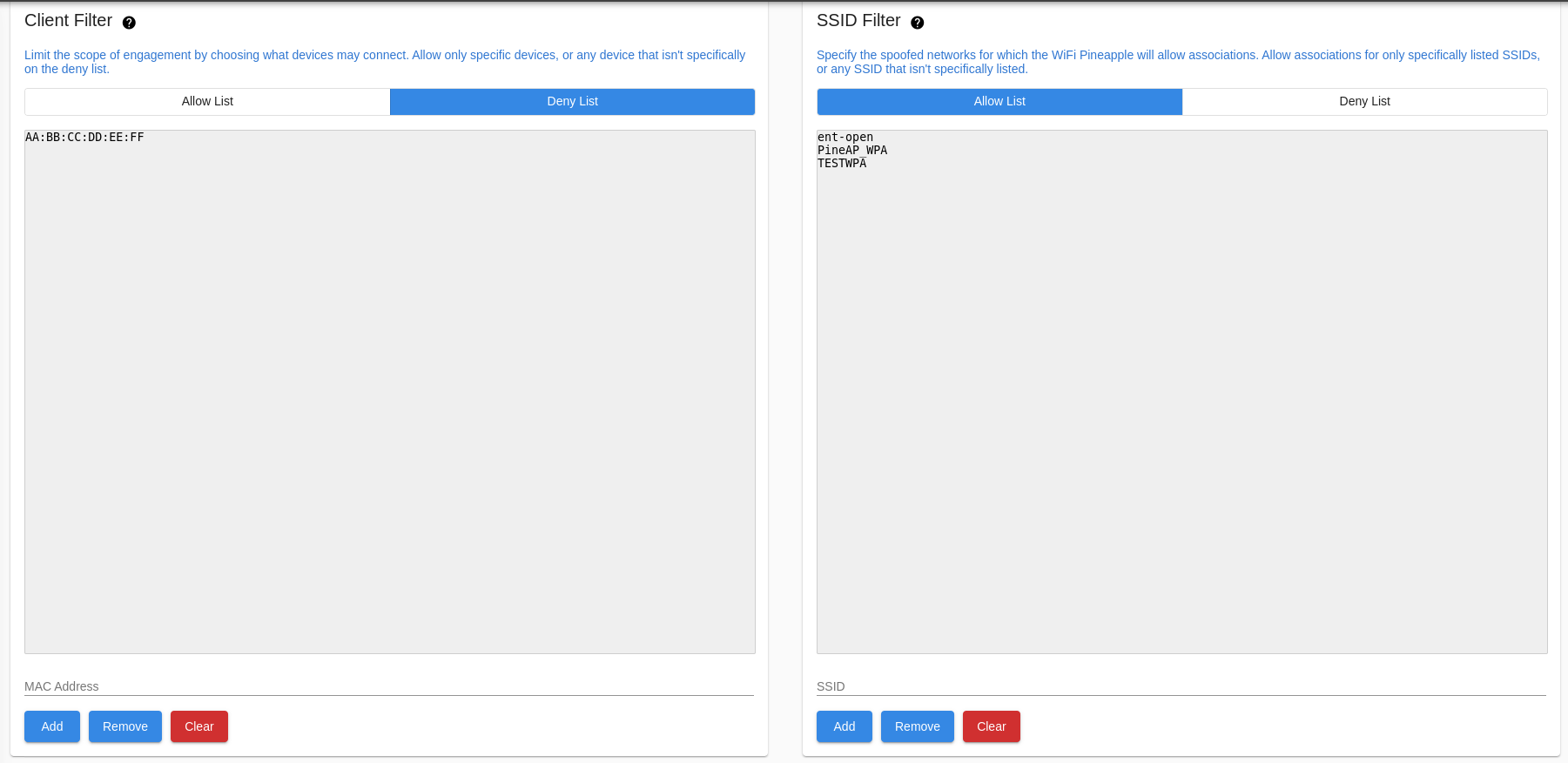
PineAP Filtering
Access Points
The Access Points tab controls the behavior of the EvilWPA access point
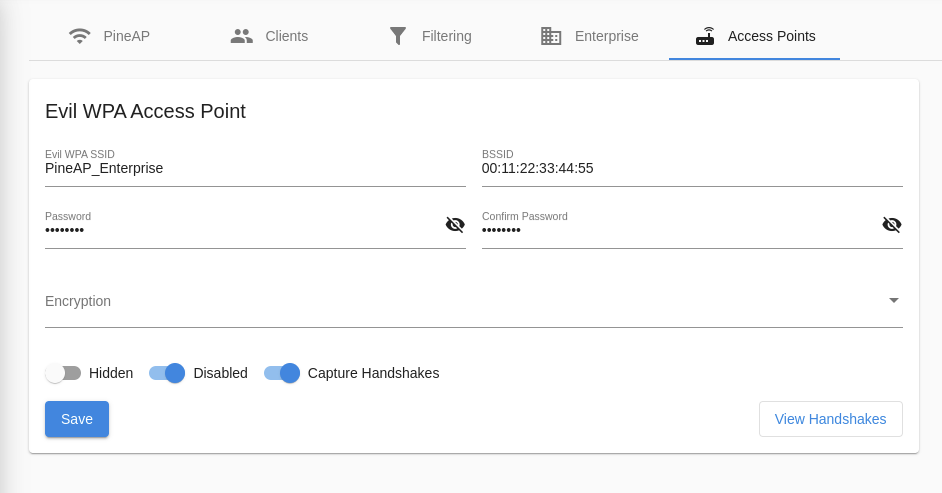
Basic EvilWPA Access Point Configuration