Recon
Scanning
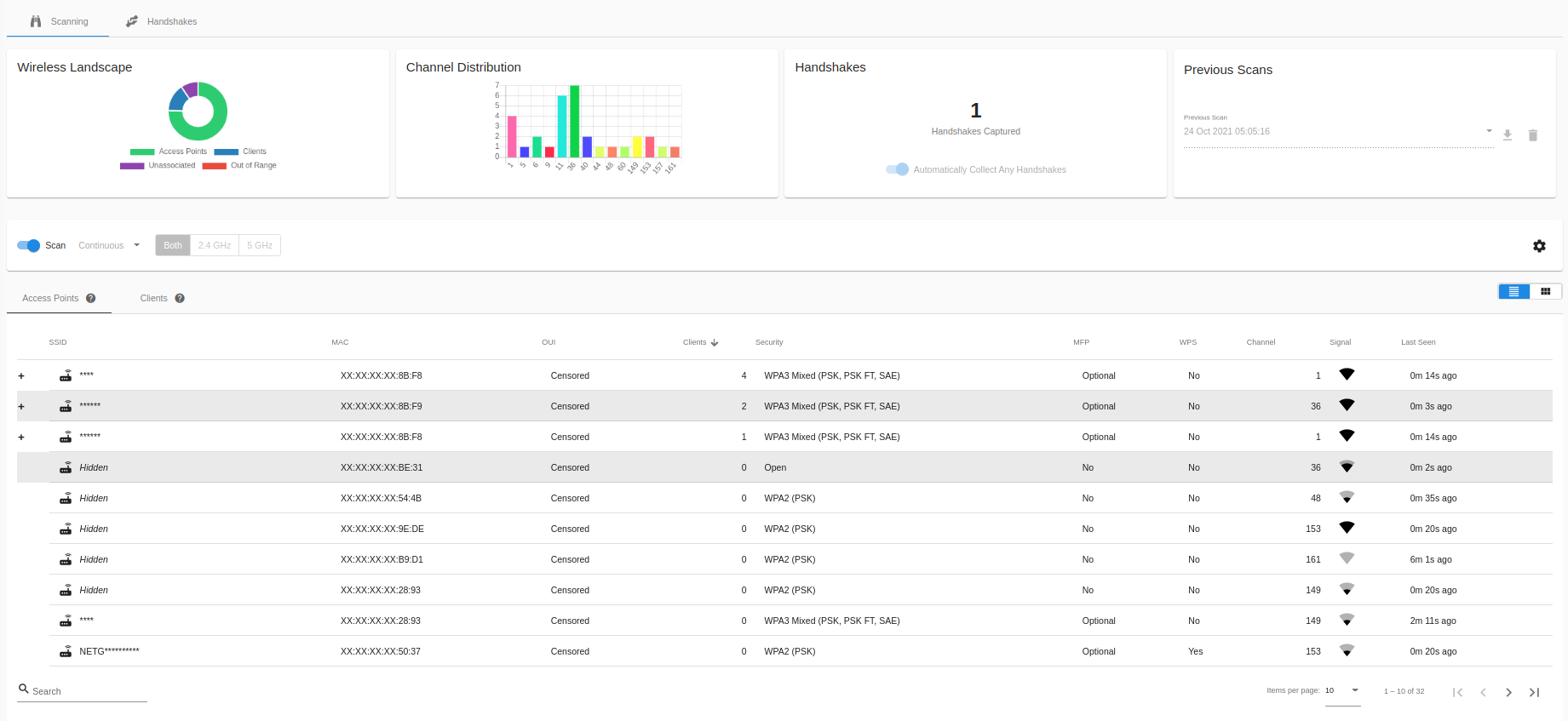
On the main Recon page, you can see an at-a-glance overview of the current wireless landscape, with a list of discovered APs and their associated clients, unassociated clients, and clients that have gone out of range in table form.
To change to a mobile friendly view, select the card button next to the table icon in the Access Points & Clients card.
Wireless Recon
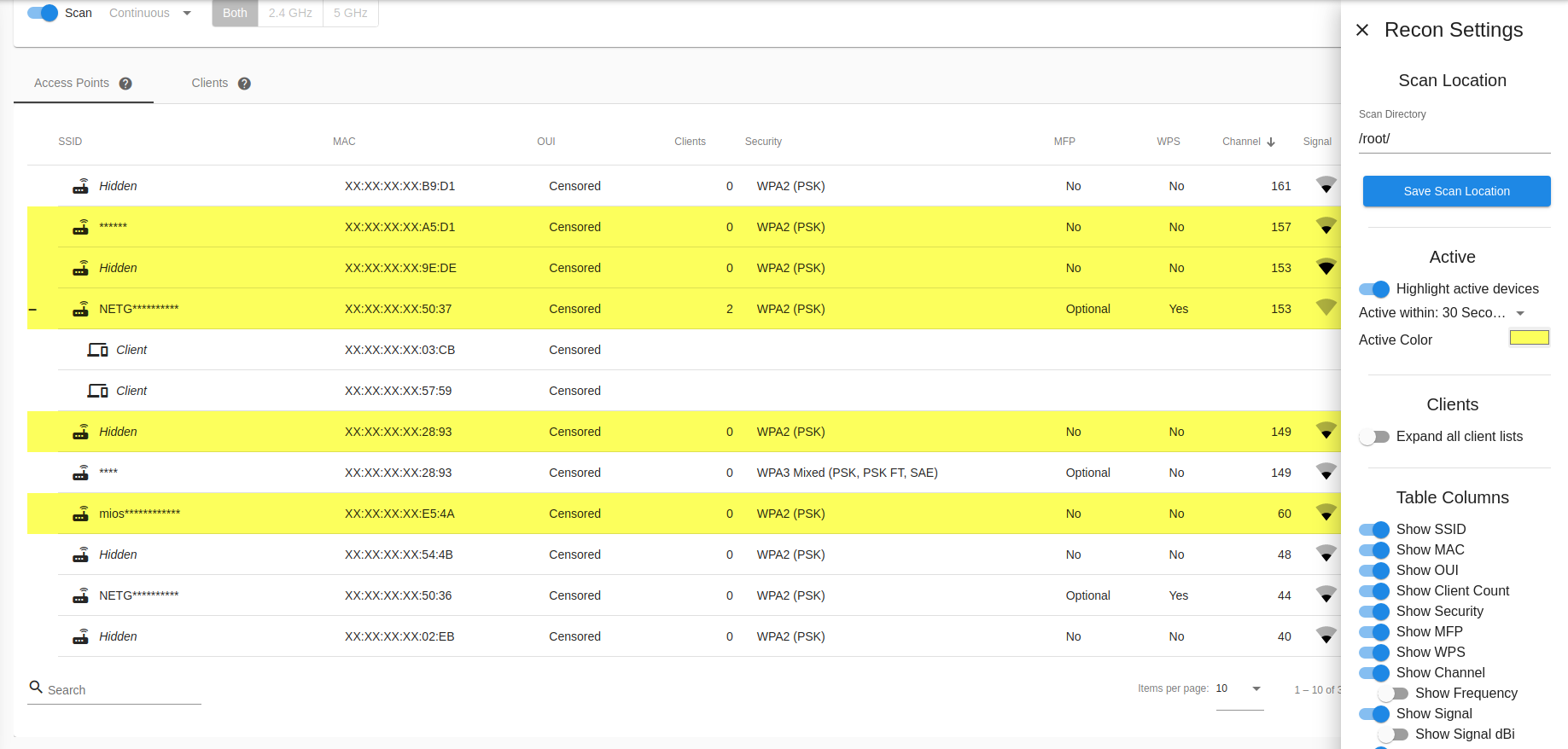
You can change Recon settings, such as scan location and displayed table columns, by selecting the Settings gear icon on the right side of the Settings card.
Clicking on a column header allows sorting by that column. The number of Access Points or Clients shown can be controlled by the Page Size option below the view.
You can search for Access Points or Clients by SSID, BSSID, or MAC address via the Search field below the view.
In the Access Point view, if clients have been discovered on an Access Point, clicking the + icon for that row will expand the row and show the list of clients. Clicking on the - icon will collapse an expanded row.

Expanded client list
You can expand all clients automatically by going to the Recon Settings via the gear icon, and choosing “Expand all client lists”
Active Access Points and Clients can be automatically highlighted to make finding them easier; click on the gear icon to open the Recon Settings and turn on “Highlight Active Devices”. Pick an activity time, and a highlight color that makes you happy!
By clicking on an AP or Client in the list, a side menu will slide out from the right. From here you can select options specific to the type of device you selected, such as capturing handshakes or cloning, or adding MAC addresses to the Filters.
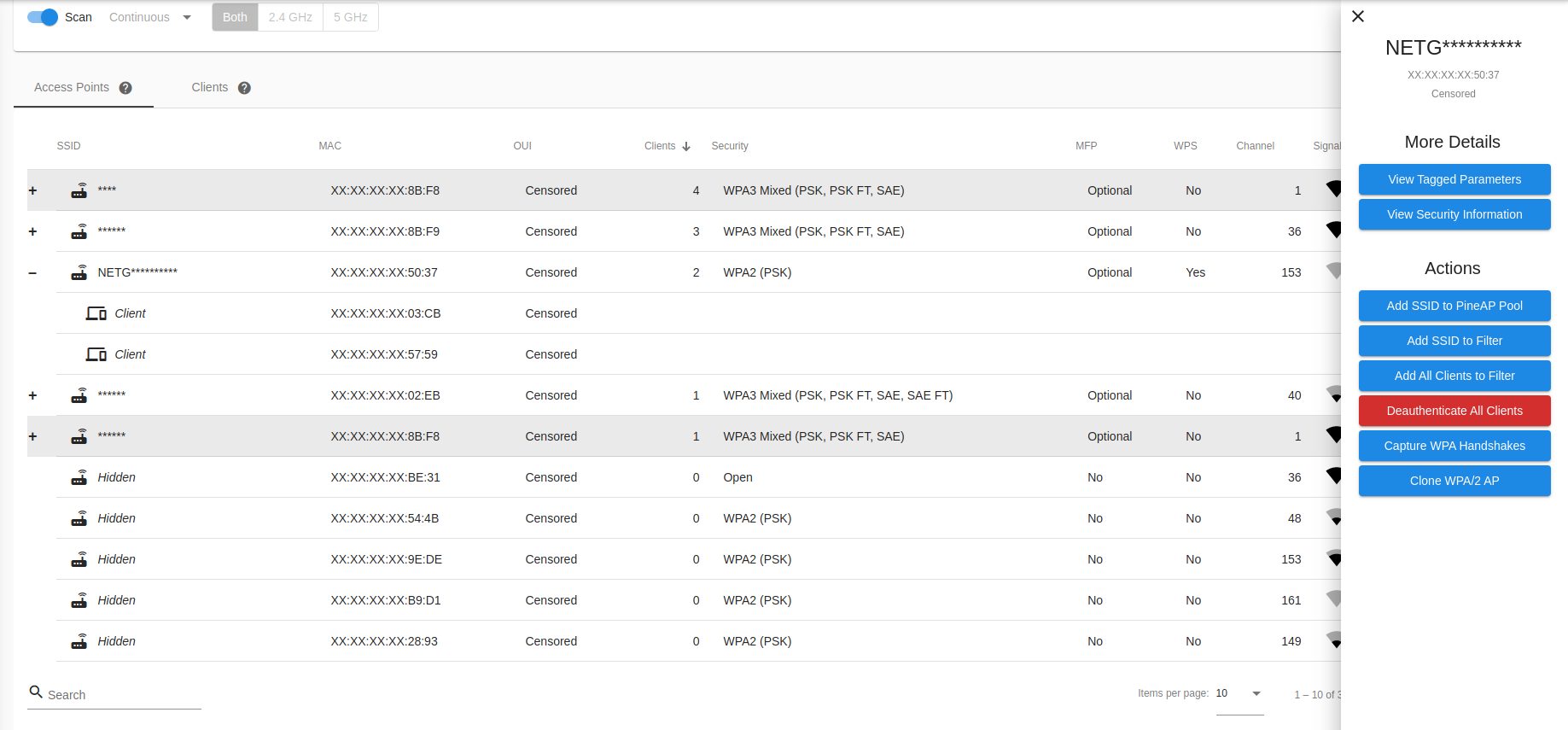
Access point details
Tagged Parameters
The tagged parameter views offers an in-depth look at the exact parameters advertised by the network.
Tagged parameters are included in the beacon packets which advertise a WiFi network, and contain information about the encryption, channel selection, surrounding traffic, and more.
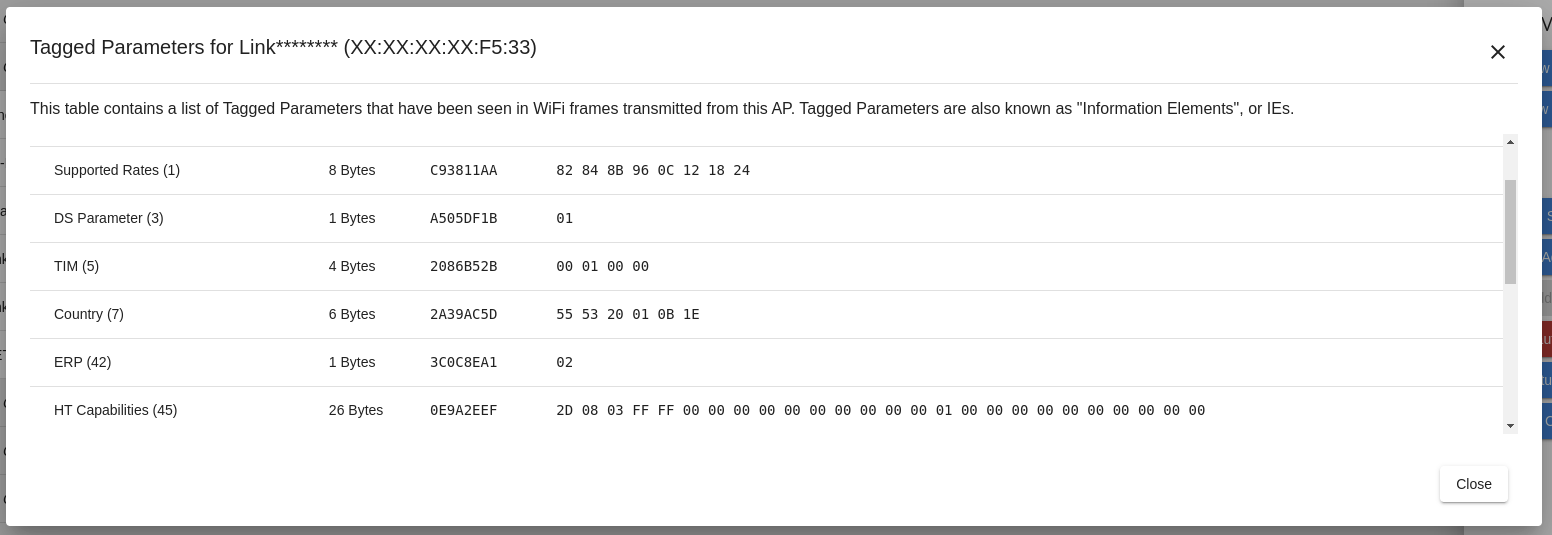
Example tagged parameters
Security Information
The security information panel offers a simplified explanation of the security options employed by the network.
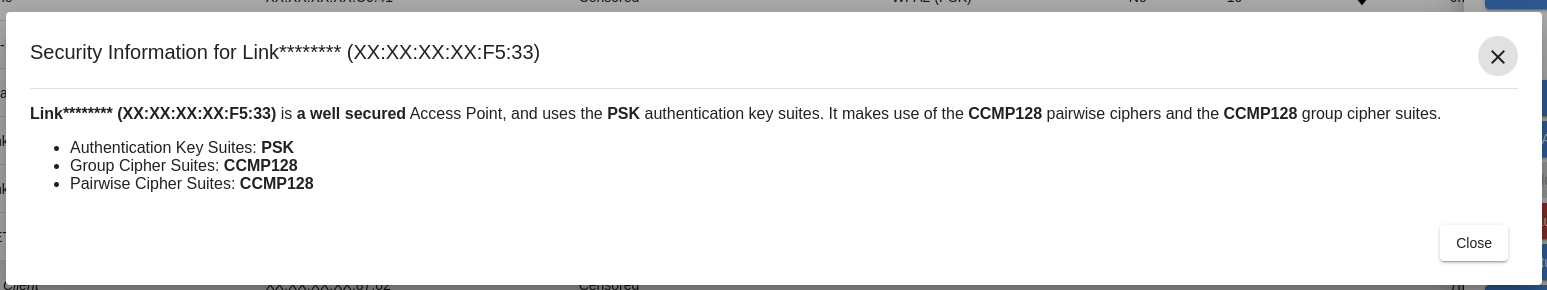
Example security information
Deauthenticating Networks and Clients
Deauthenticating clients sends a forged WiFi packet which indicates that the client is no longer authorized on the access point.
The WiFi Pineapple can deauthenticate all clients on an access point, or specific single clients.
Deauthenticating a client can be used to migrate the client to another access point, such as the EvilWPA/2 Twin access point. It can also be used to cause a client to reconnect to a network, generating a WPA Handshake.
Deauthenticating clients and networks is not possible when:
- There are no clients on the network.
- The client or network uses MFP, or Management Frame Protection. MFP is an extension to the WiFi standards which is designed to prevent impersonation of an access point. This prevents forged deauthentication packets from being respected by the client.
- The client or network is on a restricted channel. The FCC and other regulatory bodies around the world enforce extremely strict limits on part of the 5GHz band known as DFS / UNII-2 / UNII-2e which prohibits transmission on these frequencies if not communicating with an access point.
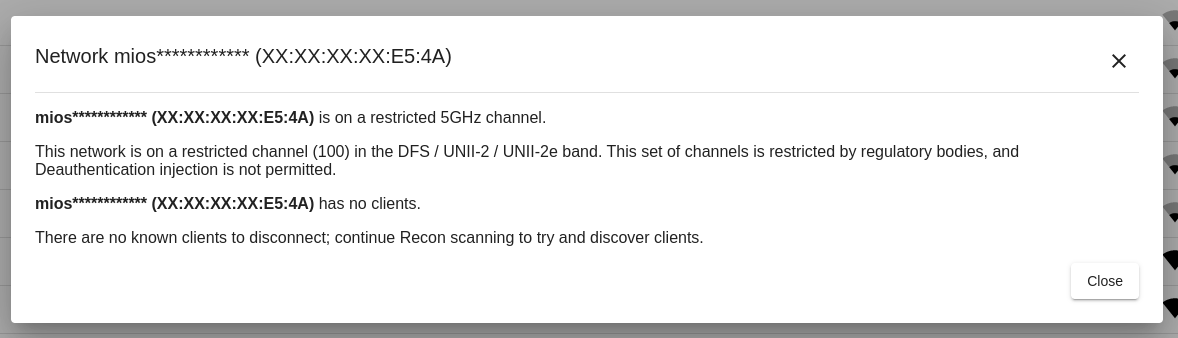
An example warning when deauthentication is not possible
Handshakes
The Handshakes tab shows any captured handshakes. Handshakes are captured in PCAP and Hashcat’s 22000 format.
Handshakes that list Recon Capture as the source show that they were captured during a Recon scan or a Recon handshake capture.
Handshakes captured from the Evil WPA AP show as Evil WPA/2 Twin.
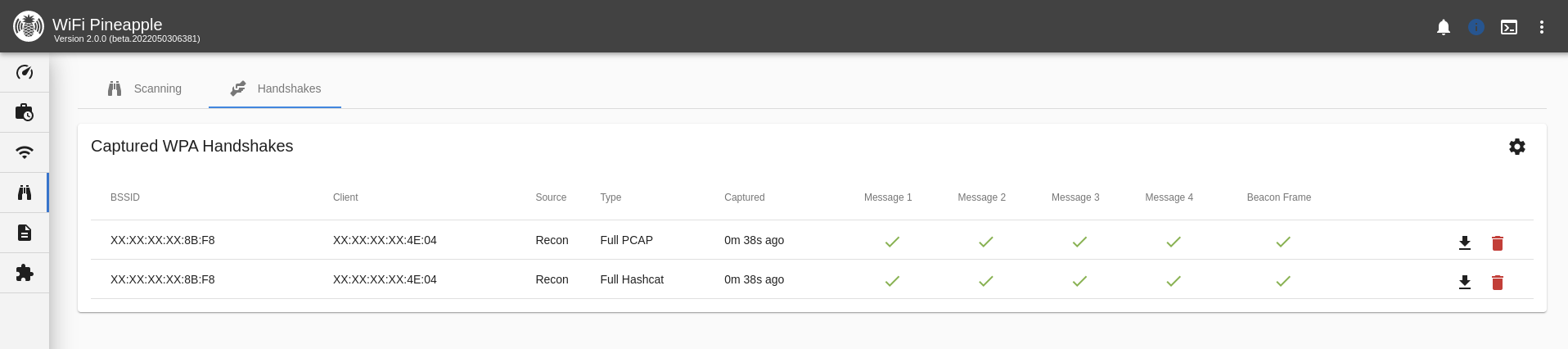
Handshake capture
You can change where the handshakes are saved on the WiFi Pineapple by clicking the Settings icon.