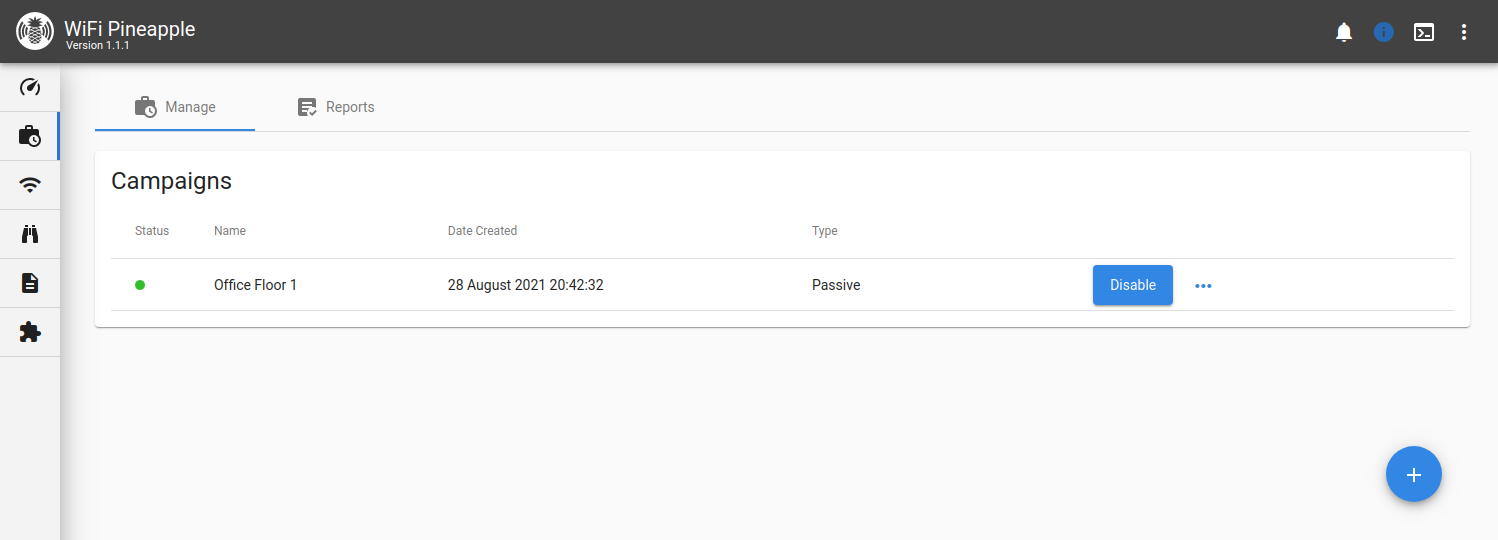
Campaigns
Manage
Campaigns that have been created are listed in a table, showing the current status, name, creation date and campaign type. You can enable or disable your campaigns with the Enable/Disable toggle, and edit or remove them by clicking the “…” menu button.
Campaign Modes
Reconnaissance - Monitor Only
Passively monitor client device and access point activity within a defined region of the WiFi environment.
Client Device Assessment - Passive
Identify client devices susceptible to basic rogue access points or evil twin attacks. Uses a passive PineAP mode to mimic access points only upon direct request. Depending on filter configuration, client devices may be allowed to associate with the WiFi Pineapple.
Client Device Assessment - Active
Identify client devices susceptible to advanced rogue access points or evil twin attacks. Uses an active PineAP mode to broadcast an SSID pool, mimicking all access points listed. New access points may be dynamically added to the pool. Depending on filter configuration, client devices may be allowed to associate with the WiFi Pineapple.
Editing Campaigns
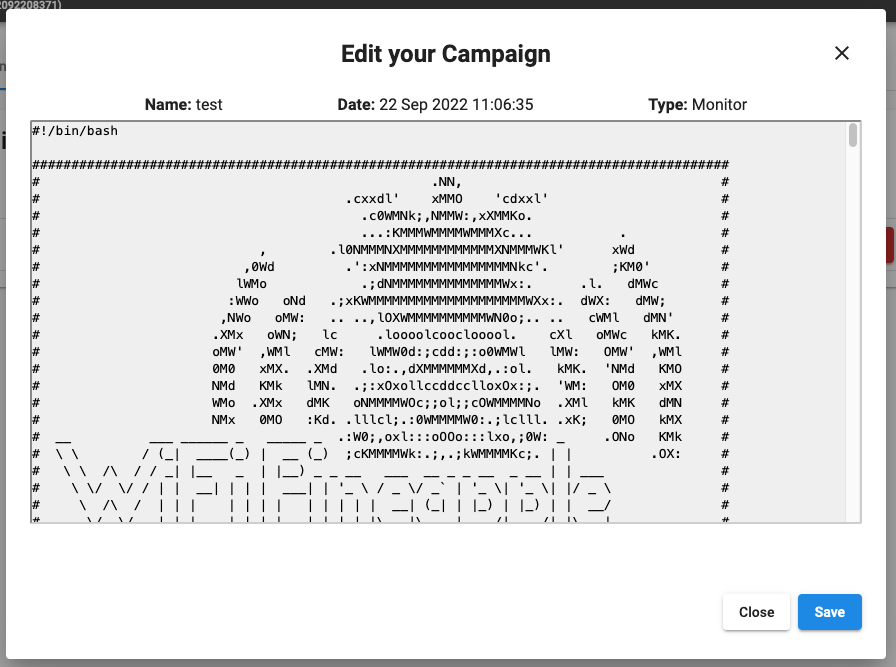
Campaign script editor
The campaign shell script may be modified and extended upon by opening the campaign script editor from the campaign’s “…” menu. Campaigns reside in /etc/pineapple/campaigns/ and are generated using the /etc/pineapple/campaign-template.sh base script file.
Reports
From the Reports tab, you can download and delete the reports that have been generated by your campaigns.
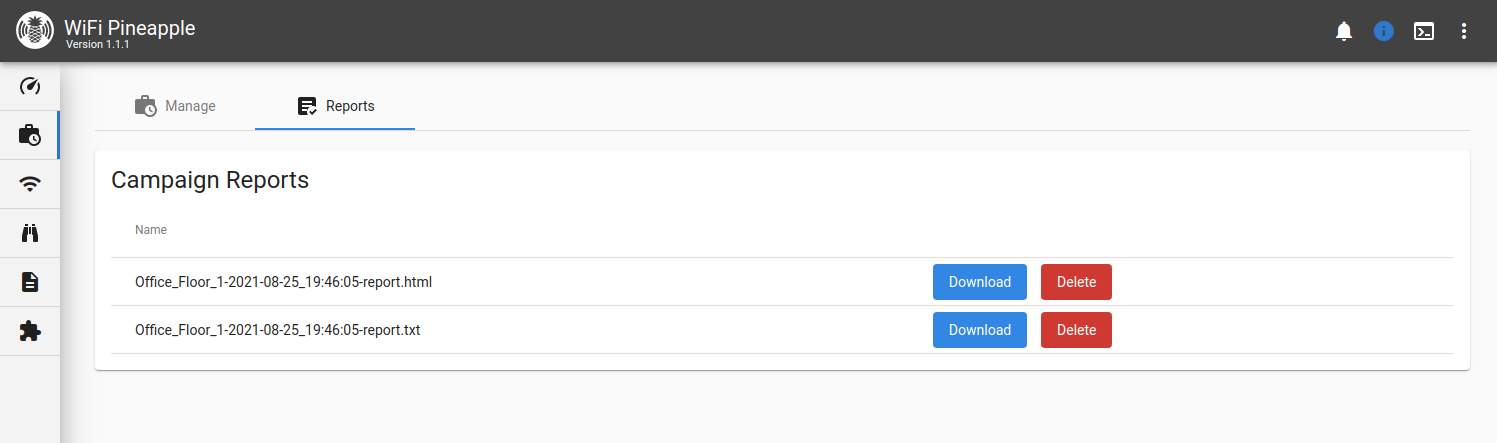
Campaign reports
Storage and Transmission
By default, reports are saved to the local disk under /root/loot/. Additionally, reports may be sent to a connected Cloud C² server, or by email with a configured SMTP server.
Email Reporting
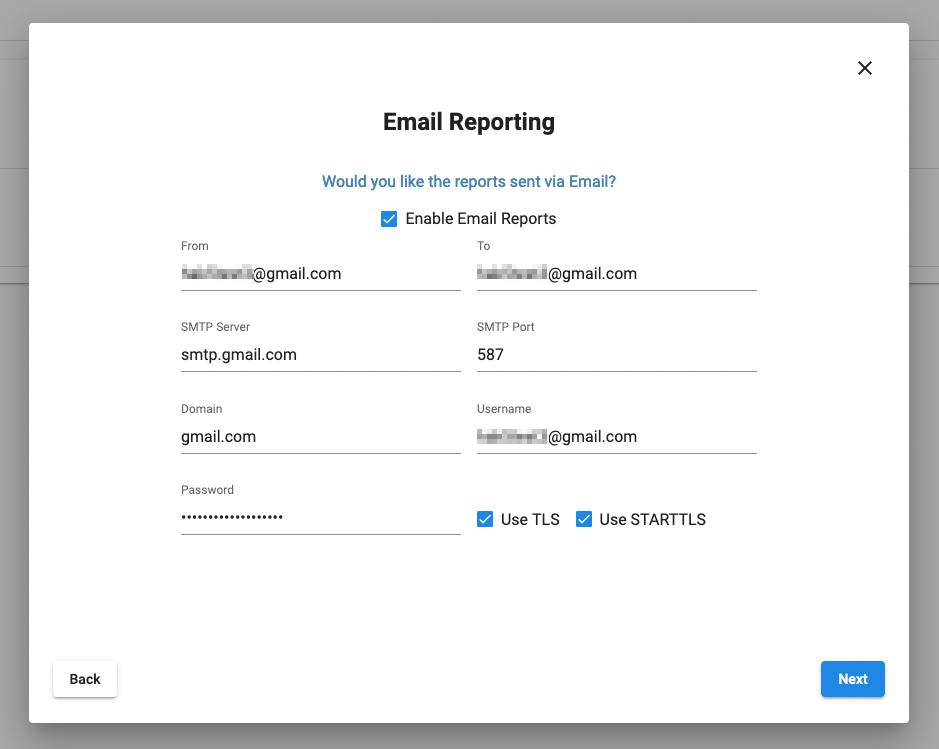
Email reporting with a SMTP configuration for Gmail
Reports sent by email require SMTP configuration. Emails are sent via msmtp with optional support for TLS and STARTTLS.
Gmail users: to use Google’s SMTP server, the account must have 2FA enabled, an App Password, and IMAP enabled. See: https://support.google.com/mail/answer/7126229 and https://support.google.com/accounts/answer/185833
Cloud C² Exfiltration
The campaigns system may be configured to use the C2EXFIL utility to exfiltrate reports to a configured Cloud C² server. The reports will reside within Cloud C² from the device’s loot tab.
Formats
Reports may be generated in either JSON or HTML format.
- JSON: Report data in JSON format, for parsing with other tools.
- HTML: A full HTML report, containing tables and formatting.
Captured handshakes may be included in HTML reports as downloadable base64 links.