Shark Jack Basics
The Shark Jack is a portable network attack and automation tool for pentesters and systems administrators designed to enable social engineering engagements and opportunistic wired network auditing. It features a familiar Hak5 payload architecture, flip-of-the-switch operation and multi-color LED for instant feedback.
This documentation serves both cable and battery variants of the Shack Jack with notable differences highlighted.
VARIANTS
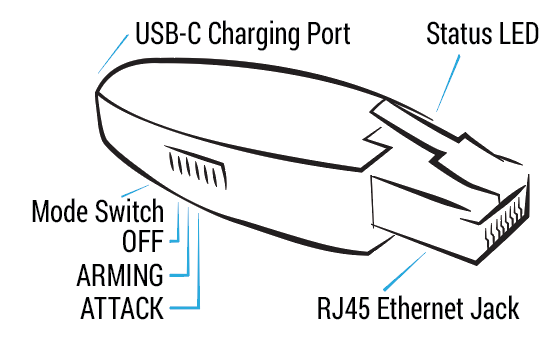
Shark Jack
The original Shark Jack is a battery powered device with a 10–15 minute runtime and feedback via RGB LED. It’s as comfortable on the keychain as it is in your EDC.
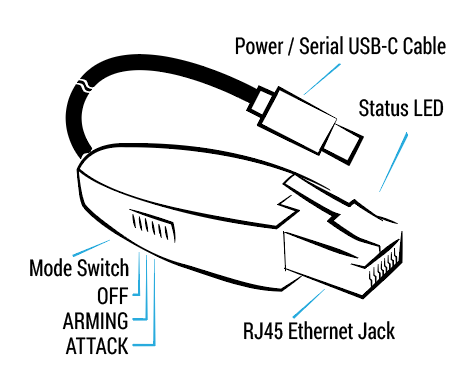
Shark Jack Cable
The Shark Jack Cable is a USB-C powered pentest companion with continuous runtime and feedback via RGB LED and an interactive serial console. It can be planted for long-term headless deployments or run temporarily from a battery source. This can include the operators USB-C powered smartphone ¹, which may enable shell access via serial using a third party app ².
- ¹ smartphone compatibility may vary. Tested with 2021-era flagship Android devices.
- ² serial access on Android tested using the third party Serial USB Terminal app.
Shark Jack Cable Android Serial Setup
Recommended apps: Hacker’s Keyboard, Serial USB Terminal.
DEPLOYMENT
The Shark Jack is meant to be deployed against a target network for brief reconnaissance, exfiltration and IT automation tasks. With a fully charged battery, the Shark Jack will operate for about 10-15 minutes. The Shark Jack Cable may run for as long as a standard USB-C power source is available.
Out-of-the-box, a pre-installed default payload executes an nmap scan of the connected target network when the switch is in the attack mode. This default payload saves the scan results to a loot directory on the device.
This loot may be recovered from SSH access when the switch is in the arming mode. Further, with the switch in arming mode the default payload may be replaced with your own payloads, written in bash, or payloads downloaded from the community repository at https://github.com/hak5/shark-payloads
The Shark Jack Cable provides real time access to loot and the ability to download and activate payloads over-the-air by an interactive serial shell.
CHARGING
The Shark Jack features a non-removable lithium ion battery. Please read all instructions before use and familiarize yourself with the important safety information and warnings.
To charge the Shark Jack, flip the switch to the OFF / Charging position. Plug the Shark Jack into a standard USB power source using a USB-C cable. After a brief boot period, indicated by a flashing green LED, the Shark Jack will begin charging.
When the device is charging, the LED will blink blue. When the device is full charged, the LED will light solid blue - at which time the device should be disconnected from USB power. Do not overcharge, and do not leave unattended while charging.
The Shark Jack cable does not feature an internal battery and does not require charging. The switch positions are the same for both Shark Jack and Shark Jack Cable.
MODES OF OPERATION
Similar to many Hak5 tools, the Shark Jack features an Arming mode and an Attack mode. In Arming mode, the Shark Jack is accessible from SSH for payload loading and configuration. In Attack mode, the selected payload is executed.

ATTACK MODE
In attack mode, the Shark Jack will execute the payload.sh or payload.txt bash script from /root/payload. Most payloads specify a network mode, setting the Shark Jack as a client with NETMODE DHCP_CLIENT or a server with NETMODE DHCP_SERVER.
ARMING MODE
In arming mode, the Shark Jack will be configured with a static IP address of 172.16.24.1 and will start an SSH server.
With the Shark Jack in arming mode, you may access the embedded linux system via SSH. Connect the Shark Jack to your computer’s Ethernet interface, specify a static IP address in the 172.16.24.0/24 range for this interface (for example 172.16.24.2) then establish an SSH connection to the Shark Jack at 172.16.24.1 (e.g. with the command “ssh root@172.16.24.1”)
The Shark Jack Cable provides access to the shell in arming mode via its dedicated serial console. When connected, press ENTER to activate the shell and run HELP for a list of payload and firmware management commands.