Openvpn Payload
The OpenVPN payload for the Packet Squirrel can provide remote access or client tunneling.
Remote Access
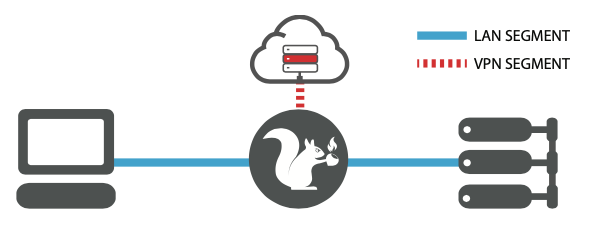
The first, default behavior, is to provide remote access into the network. In this mode the target plugged into the “Ethernet In” port on the Packet Squirrel will have access to the network plugged into the “Ethernet Out” port without interruption. Meanwhile, an OpenVPN connection will be established – typically to your server on the Internet – enabling remote access into the Packet Squirrel.
Client Tunneling
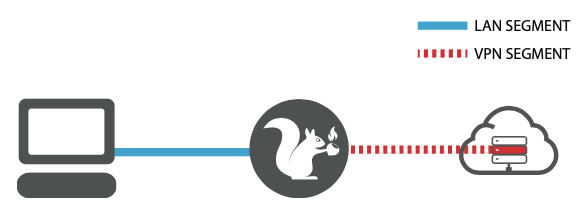
The second, optional behavior, is to tunnel all of the traffic from the target device plugged into the “Ethernet In” port through the configured OpenVPN connection. This is configured by editing the /root/payloads/switch3/payload.sh file and changing line 5 to FOR_CLIENTS=1
In either mode the SSH server on the Packet Squirrel will be enabled for remote access.
SERVER SETUP
Begin by setting up an OpenVPN server, typically on a VPS or dedicated server with a static IP address. For reference, see the Hak5 youtube playlist titled “Hak5: VPNs – Everything You Need to Know” or search for Hak5 episode 2022 for a 5-minute OpenVPN install script.
Try the OpenVPN installer from https://github.com/Nyr/openvpn-install
From a shell on your new VPS or dedicated server on the Internet, issue:
wget https://git.io/vpn -O openvpn.sh && bash openvpn.sh
Accept all of the defaults and in a few moments a client.ovpn file will be created.
CLIENT SETUP
With the server setup, generate a new client certificate file and copy it to the Packet Squirrel in /root/payloads/switch3/config.ovpn
Quick Setup: SSH into the Packet Squirrel in Arming Mode and have it copy the client.ovpn file from your OpenVPN server to the OpenVPN payloads config.ovpn file using SCP (Secure Copy)
scp user@server:client.ovpn /root/payloads/switch3/config.ovpn
DEPLOYMENT
With the OpenVPN server ready and the client on the Packet Squirrel configured, flip the selector switch to position 3 and deploy inline between a target and network in the same manner as the previous Packet Capture and DNS Spoof examples. When the OpenVPN connection is established the Packet Squirrel will blink yellow.
If you’re using the Client Tunneling mode there’s no further configuration necessary. To test the connection, for example if the target is a computer, try browsing to one of the many IP address testing sites like ipchicken.com to verify that the connection is being tunneled through the VPN.
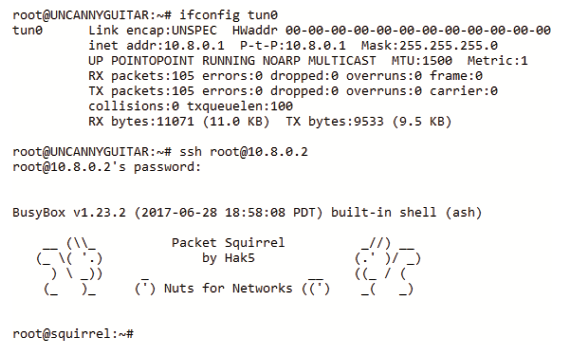
If you’re using the Remote Access mode, the Internet connection of the target will not go through the VPN. Rather, the VPN may be used to SSH into the Packet Squirrel. To do so, begin by connecting to the VPN server via SSH and determine the IP address of the Packet Squirrel on its OpenVPN network. Typically this is the incremented one following the IP address of the OpenVPN servers tunnel interface. For example, on the OpenVPN server issue ifconfig and look for a tun0 interface. The default address is 10.8.0.1. From there, SSH into the Packet Squirrel as root at 10.8.0.2.\